Privacy enhancing technologies (PETs) can increase access to data that may otherwise be kept closed for reasons of privacy, commercial sensitivity or security concerns. With the support of the Patrick J. McGovern Foundation, our work in this area will drive the use of PETs to enable safe and secure data use for positive economic, social and environmental impact.
What are PETs and why are they important?
PETs are tools and practices that can enable access to data that may otherwise be kept closed for reasons of privacy, as well as commercial sensitivity or national security.
At the ODI, we adopt a broad interpretation of the term. Some PETs have long been used, such as invisible ink, redaction, pixelation and voice obfuscation. Some of these represent tried and tested approaches, used across many different contexts and sectors.
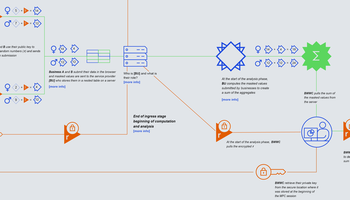
Over recent years, there’s been an explosion of new tools and practices for enabling safe and secure access to data, including differential privacy, federated learning, secure multi-party computation, secure enclaves and trusted execution environments.
At the launch event in July, Calum Inverarity (ODI Senior Researcher) explained why the ODI is starting this programme to explore these novel technologies, how they can tip the balance in the favour of people exploited in the current system and the utility that has already been proven.
What our PETs programme aims to achieve
The programme is designed to drive the use of PETs to enable safe and secure data use for positive economic, social and environmental impact.
To do this, we will:
- Increase awareness of different types and forms of PETs, particularly among audiences who are unfamiliar with them.
- Increase understanding about the challenges these technologies can help address, as well as their limitations.
- Support the application of these technologies to address significant economic and social challenges.
- Ensure effective interventions are made by policymakers, funders and other actors to address barriers to the adoption of PETs.
Where do PETs come from and how are they used?
A number of novel PETs have emerged from academic research and have diffused quickly into real-world applications. Wide-scale adoption could be transformative in unlocking the value of data that has traditionally been considered too sensitive to share. They’ve already demonstrated their utility across multiple sectors for the delivery of both public and private services. Examples include:
- Combating human trafficking - Enveil and DeliverFund used homomorphic encryption-based technology to provide safe access to a large human trafficking database. Users of the database can securely cross-match and search DeliverFund’s extensive data holdings without ever revealing the contents of the search itself or compromising the security and ownership of the underlying data.
- Delivering research at scale whilst respecting patient confidentiality - OpenSAFELY is a secure, transparent, open-source software platform for analysis of electronic health records data. It has enabled risk factors associated with COVID-19 to be identified, without exposing the personal information of individuals.
- Using real data for large-scale statistical study whilst protecting privacy - The Estonian Center of Applied Research (CentAR) conducted a study using secure multiparty computation on data from the Estonian Tax and Customs Board and Ministry of Education and Research to look for correlations between working during university studies and failing to graduate in time.
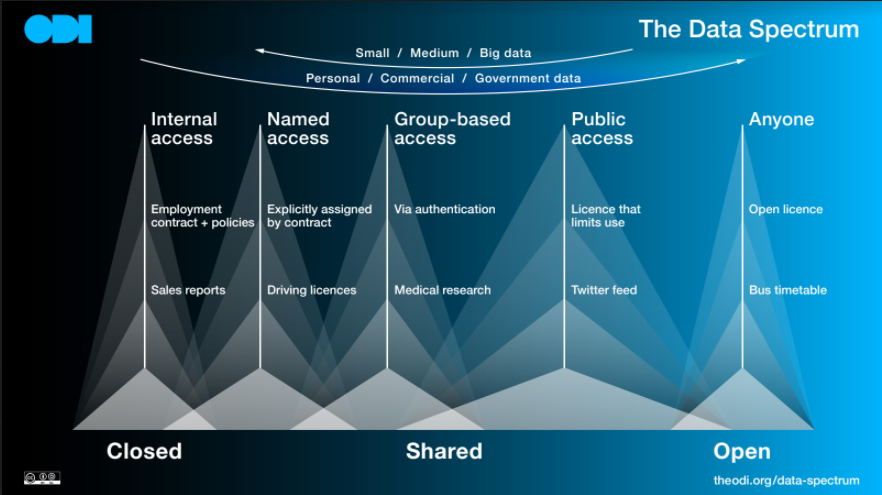
They also offer promise as tools and practices to help organisations adhere to new data protection laws, such as the General Data Protection Regulation and California Consumer Privacy Act. Furthermore, with the increased use of PETs, we may see sensitive data – where access has been limited to internal, or narrow sharing (as denoted below in the Data Spectrum) – being made available securely for analysis in a privacy preserving manner.
Despite their potential, PETs often remain inaccessible to organisations with limited technological knowledge and financial resources to procure such solutions. At the ODI, we believe that there is a need for independent scrutiny and guidance of these technologies to understand their potential impact, limit their misuse and to make them more accessible.
We also think the prospect of the wider adoption of PETs raises significant questions around governance, trust and assurance. For example, what types of value are they being used to create and who are the beneficiaries of it? Relatedly, these have potential for great commercial applications, such as privacy-preserving personalisation of services, but how might we avoid this becoming the be-all and end-all of these technologies? Finally, there are some exciting – albeit early stage – ideas on how some PETs might facilitate greener machine learning, which may prove to be particularly relevant as the development and interest in large language models continues to grow. We are interested in exploring what other problems these technologies might help solve.
While the PETs we have discussed have a number of different – often complementary qualities – when used in combination that can make them suitable for use in a variety of contexts, the essential commonality they share is enabling access in a way that ensures that privacy is not compromised.
In a discussion at our recent summit, we considered some of these developments.
Our work so far
Over the years, we’ve worked with a wide range of organisations on approaches to enable secure and safe access to data - including using PETs. This includes: research on different approaches, methods and tools to preserve privacy; publishing explainers on how organisations facilitate safe access to sensitive data; collaborating with other organisations to explore the value, opportunities and real-world challenges to deploying PETs; and producing practical guidance on how to deploy privacy enhancing technologies.